HIPAA Compliance Checklist for 2025

Managing SaaS has become complex due to evolving organizational requirements. It becomes more challenging with the widespread adoption of new applications and collaboration with external organizations. Therefore, it's essential to ensure such tools and resources are secure and not compromised.
Unauthorized employee access to SaaS apps can cause harm, and hackers may breach your systems to steal data. Therefore, you should use credential entitlement management (CEM) to strengthen identity management and governance within your organization.
Robust entitlement management software helps enforce these controls across your SaaS environment, ensuring data isn’t exposed through unmanaged permissions.
CEM automates processes such as handling access requests, assignments, reviews, and expirations. It identifies appropriate access levels and reduces access retention risks for internal and external users.
This guide will help you implement CEM effectively, from basics to advanced strategies, ensuring secure and optimized access rights management.
TL;DR
- Entitlement management defines and controls user access rights within an organization, ensuring secure and appropriate access to systems and resources.
- Credential entitlement management (CEM) automates the processes of access provisioning, de-provisioning, and reviews, enhancing security and operational efficiency.
- Effective entitlement management reduces risks by enforcing least privilege principles, monitoring access patterns, and ensuring compliance with security policies and regulations.
- CloudEagle.ai automates access management tasks like user provisioning, role-based access control, and access reviews to streamline operations and mitigate risks.
- Implementing an automated CEM system with tools like CloudEagle.ai helps maintain security, boost productivity, and ensure regulatory compliance.
What is Entitlement Management?
Entitlement Management involves the systems and procedures for overseeing, regulating, and tracking access permissions, or "entitlements," granted to users, applications, or systems within an organization’s IT infrastructure. These entitlements determine which resources, such as applications, databases, or cloud services- a user can access and the specific actions they can take, like viewing, modifying, or deleting data.
By aligning access with a user’s role, duties, and company policies, entitlement management upholds the least privilege principle, bolstering security and ensuring compliance.
Effective entitlement management involves several key aspects:
- Clearly defining the access rights for different roles or user groups.
- Assigning these access rights to users based on their roles and responsibilities.
- Regulating and monitoring resource access using control mechanisms like RBAC or ABAC.
- Regularly reviewing access patterns to align with organizational policies and regulatory requirements.
- Promptly removing access rights when they are no longer needed or appropriate.
With the help of comprehensive entitlement management solutions, these tasks become faster, more accurate, and scalable, especially in SaaS-heavy organizations.
What is entitlement in identity management?
Entitlement in identity management refers to the rights or permissions granted to users or entities within a system or application. These permissions dictate what actions they can perform, what resources they can access, and under what conditions they can do so.
In IAM systems, managing entitlements involves:
- Giving users or groups the right permissions based on their roles.
- Checking and auditing assigned rights to ensure they're correct and meet current needs.
- Removing or changing permissions when roles change, employees leave, or access requirements shift.
What Can I Do with Entitlements Management?
Entitlement management helps you control and automate user access to systems and resources, enhancing security, ensuring compliance, and improving operational efficiency.
It lets you define who has access to what, when they can access it, and under what conditions across your organization’s applications and infrastructure.
Enhance Security
Managing SaaS access effectively is essential to prevent unauthorized entry, protect sensitive data, and ensure compliance with security policies. Organizations can maintain a secure environment and uphold regulatory standards by controlling who has access, encrypting sensitive information, and regularly reviewing access permissions.
Entitlement management offers several key benefits that enhance your organization's security. It also prevents unauthorized access, protects sensitive data, and ensures compliance with security policies. It provides you with the following:
- Granular access control: Manage access based on roles and responsibilities to reduce unauthorized access.
- Centralized management: Simplify administration by managing access rights across systems and applications from a single point.
- Reduced data breach risk: Enforce the least privilege to minimize attack surfaces and insider threats.
- Monitoring and auditing: Track access, detect anomalies, and ensure compliance with regulatory standards.
- Adaptive access control: Adjust privileges based on user context for enhanced security and user experience.
- Access revocation: Quickly revoke access rights to mitigate risks when roles change or employees leave.
Streamline Access Control
With proper access control mechanisms, you can enhance your organization’s operational efficiency. When you streamline access control, it simplifies user access management where only authorized users gain access. It helps you minimize security risks in your organization.
You can leverage automation for seamless user provisioning and de-provisioning. Also, establish stringent security policies to restrict access to critical resources. Ensure your chosen tool integrates smoothly with your existing IT infrastructure to maintain operational continuity.
As your organization grows, you must apply the least privilege principle to simplify access management. You can do this using role-based access control (RBAC) based on job roles.
You can automate access changes with predefined rules to ensure consistency and minimize errors. Easily revoke access when roles change or employees leave, and keep detailed audit trails to boost compliance and security.
Improve Operational Efficiency
Streamlined access management reduces admin overhead and boosts user productivity. It also ensures seamless onboarding and offboarding in your organization.
Here’s how your organization can achieve these benefits:
Reduce administrative overhead: You can automate access workflows to simplify provisioning and de-provisioning tasks. Centralizing access controls across systems saves time and reduces complexity. It enables users to make self-service access requests based on predefined roles.
Enhance user productivity: Streamline access provisioning to quickly onboard new employees or adjust roles. It helps grant fast access to essential resources based on job responsibilities. You can use RBAC to ensure users have the right tools without unnecessary permissions.
Streamline onboarding and offboarding: You can automate onboarding processes to promptly grant necessary access to SaaS tools. Also, you can opt for automated de-provisioning to revoke access rights promptly upon employee departure. It reduces security risks and maintains compliance with organizational policies.
Ensure compliance
To ensure compliance and enhance operational efficiency, adopt a strategic approach to access management. Implement access control policies based on regulatory and organizational requirements, including the principle of least privilege. These policies minimize data exposure and ensure duty segregation to prevent conflicts of interest.
You can utilize access management systems that provide comprehensive auditing and reporting capabilities. This allows organizations to track access activities, generate audit trails, and demonstrate compliance during audits or regulatory inspections.
Integrate automated compliance checks into access management workflows. This ensures access rights align with regulatory requirements and organizational policies, reducing non-compliance risk.
Manage risks and mitigate them
You must take the necessary steps to manage and mitigate risks associated with access management to protect organizational data. You can do the following steps to identify, mitigate, and manage security risks effectively.
- Regularly assess risks to identify vulnerabilities in access management systems, applications, and data.
- Use threat modeling to predict potential attacks and prioritize security measures.
- Implement a vulnerability management program to address security weaknesses.
- Have an incident response plan for quick action during security breaches.
- Conduct access entitlements audits to ensure compliance with policies and regulations.
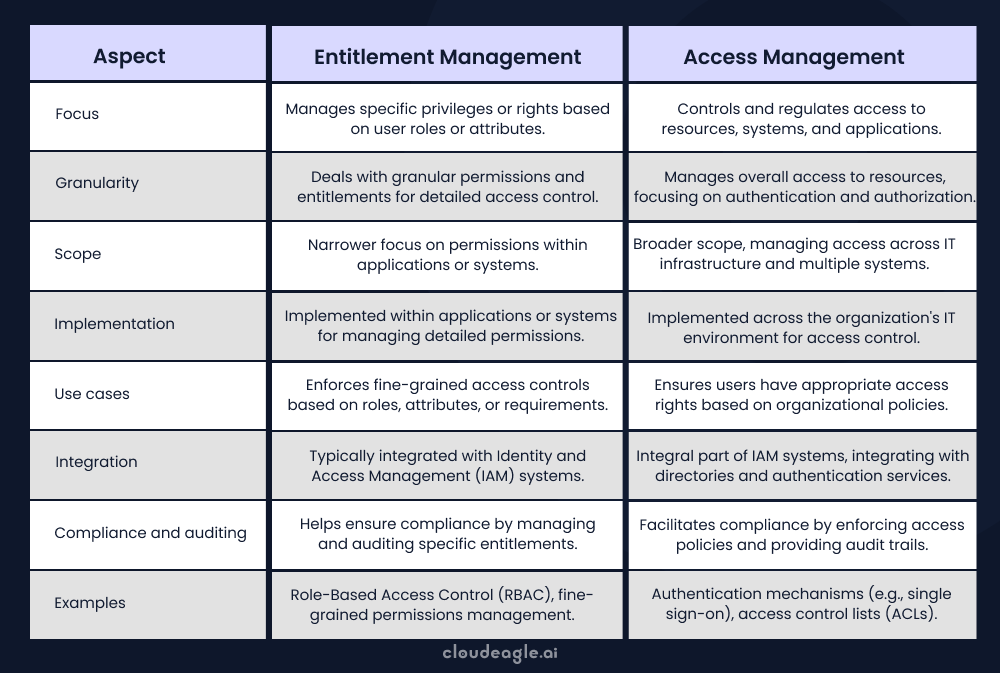
What Is the Difference Between Entitlement Management and Access Management?
Entitlement management and access management are closely linked but serve different purposes within Identity and Access Management (IAM).
Access management governs who can access which systems or applications, while entitlement management dives deeper, focusing on the specific permissions or actions each user is allowed to perform once access is granted.
What Are the Advantages of an Entitlement Management System?
An Entitlement Management System (EMS) provides key benefits such as improved security, efficient operations, and simplified access governance. It helps organizations define and control user permissions, automate access provisioning and deprovisioning, and maintain compliance with regulatory and internal security requirements.
With a proper entitlements management setup, your organization can:
- Strengthen security: Automatically enforce least-privilege access and revoke unused entitlements to minimize attack surfaces.
- Improve compliance readiness: Maintain clear audit trails and access records to meet regulations like SOC 2, GDPR, or HIPAA.
- Reduce IT burden: Automate access provisioning, deprovisioning, and approval workflows, freeing up your team’s time.
- Streamline onboarding and offboarding: New hires instantly get access to what they need, no delays or over-permissioning.
- Enhance visibility: Track who has access to what, when, and why, across your entire SaaS ecosystem.
In essence, a strong entitlement management system makes it easier to scale securely while meeting business and regulatory demands.
How Does an Entitlements Management System Work?
An Entitlement Management System is a technology solution designed to automate how access to resources, such as applications, systems, and data, is granted, monitored, and revoked. It helps ensure that users have only the permissions they need to do their jobs, maintaining a balance between security and productivity.
Here’s a breakdown of how entitlements management typically works:
- Define access policies: Roles and entitlements are defined based on job functions, seniority, or team needs.
- Automated provisioning: When a user joins or changes roles, the system automatically grants the correct permissions.
- Approval workflows: Any additional access requests are routed to the right stakeholders for review and approval.
- Monitoring and alerts: Real-time monitoring detects unusual access patterns or permission drift.
- Periodic reviews: Scheduled certification campaigns ensure that entitlements stay up to date and unnecessary access is revoked.
With a modern entitlement management software solution, all of these processes are centralized and automated, giving you real-time control over who has access to what, and why.
The Consequences of Ineffective Entitlements Management
Poor entitlement management can result in serious consequences, ranging from heightened security vulnerabilities to legal and financial fallout. When access rights aren't properly controlled, sensitive data may be exposed to the wrong users, workflows become inconsistent, and overall productivity can suffer.
Privilege Creep
Employees accumulate permissions over time that they no longer need, increasing your security exposure.
Left unchecked, this build-up of access rights can lead to violations of the least-privilege principle. Over time, it becomes impossible to know which permissions are truly necessary and which are outdated, especially when employees change roles frequently.
Audit Failures
Without a centralized record of entitlements, proving access governance during audits becomes error-prone and costly.
Auditors require clear documentation of who had access to what systems and when. If access records are scattered across spreadsheets or buried in disparate systems, demonstrating compliance becomes a nightmare.
Insider Threat Risk
Excessive or lingering access can be misused, either intentionally or by accident, resulting in data leaks or loss.
Without strict entitlements management, employees often retain access to tools and data they no longer need, giving them the opportunity to cause significant harm, intentionally or not.
Operational Slowdowns
Manual approval processes and unclear access policies slow down onboarding, project execution, and IT responses.
If employees have to wait days to gain access to the tools they need, productivity suffers. Teams lose momentum on critical projects, and IT gets bogged down with repetitive provisioning tasks.
Increased Shadow IT
Lack of visibility into access entitlements enables teams to use unauthorized tools, weakening security controls.
When employees feel they can’t get access fast enough or aren’t aware of sanctioned tools, they turn to alternative software, often without IT’s knowledge. This behavior, known as Shadow IT, puts company data at risk because these tools usually lack proper security measures and aren’t monitored.
The 5-Step Entitlement Management Process
The entitlement management process follows five key steps: defining access rights, assigning them to users, regulating ongoing access, regularly reviewing permissions, and revoking access when it's no longer needed.
This structured approach helps maintain least-privilege access, strengthening both security and compliance across the organization.
1. Defining objectives and scope for entitlement management
To build an entitlement management system, start by clearly defining the goals and objectives of the initiative. This could include enhancing security, ensuring compliance, improving efficiency, and reducing unauthorized access risks.
Identify the key outcomes you want from entitlement management, such as reducing administrative work, boosting user productivity, and maintaining security.
Also, determine which systems, applications, and resources will be included and decide whether the project will cover the entire organization or focus on critical areas.
2. Identifying stakeholders and roles
Identify the individuals, departments, or groups involved in or impacted by cloud infrastructure entitlement management. It usually involves IT administrators, security officers, department heads, and compliance officers.
Define each stakeholder's roles, like who sets access policies, implements controls, conducts audits, and handles access issues.
Make sure everyone works together to meet organizational goals, follow regulations, and use best practices in access management.
3. Inventorying user entitlements
Record all current user access rights across the organization’s systems and applications. Use tools, access logs, and interviews with admins to make a complete list.
Include roles, permissions (read/write/delete), and any linked policies. A well-structured inventory, often managed through IAM tools or entitlement management solutions, simplifies future audits and policy reviews.
4. Implementing role-based access control (RBAC) and policy enforcement
Organize users into roles based on their job functions and responsibilities. Assign specific permissions and access levels to each role, following the principle of least privilege. This approach standardizes permissions, reduces complexity, and lowers the risk of overprivileged accounts.
Create access policies for assigning, modifying, and revoking entitlements. Use automated IAM solutions to enforce these policies consistently across all systems and applications.
Implement automated workflows for granting and removing access based on roles and policies, which reduces errors and ensures compliance.
5. Monitoring and auditing entitlements
Continuously monitor user entitlements, permissions, and access activities across systems and applications in real time. Set up automated alerts and notifications to detect unauthorized access attempts or suspicious activities promptly.
Have a well-defined incident response plan in place that outlines clear procedures for handling security incidents related to entitlement management.
This proactive approach helps reduce security risks by ensuring quick detection, containment, and resolution of access-related threats.
6. Revocation and cleanup
Establish clear procedures for revoking SaaS access when users no longer need it. It can occur due to role changes, terminations, or other reasons. Document step-by-step instructions for initiating and completing the revocation process to ensure consistency and accuracy.
Promptly remove revoked entitlements from user accounts and update access permissions across relevant systems and applications. Monitor regularly to ensure that revoked entitlements are successfully removed and no longer accessible.
Streamlining Entitlement Management with CloudEagle.ai
Managing entitlements manually can quickly overwhelm your IT team and become inefficient. Tracking permissions, access levels, and user roles across multiple platforms is complex and error-prone. It leads to security risks and compliance issues.
This is where a powerful entitlement management software like CloudEagle.ai steps in, helping reduce risks, ensure compliance, and increase operational efficiency.
CloudEagle.ai can be your go-to solution for enhancing operational efficiency and accuracy in managing entitlements. It is a comprehensive SaaS management and procurement platform. The tool explicitly handles the complexities of cloud infrastructure entitlement management.
Access management: You can automate key access management aspects in your organization with CloudEagle.ai. The tool helps you simplify how IT administrators create and manage access policies.
Imagine your company has different departments, such as HR, Finance, and IT, each needing access to specific tools. For example, HR needs access to payroll systems, Finance to financial reports, and IT to system settings.
With CloudEagle.ai, you can set up policies to grant access: HR gets access to payroll, Finance to reports, etc. CloudEagle.ai handles updates automatically—if someone joins or leaves, their access is adjusted accordingly.
The tool also integrates with SSO, HRIS, and finance systems, forming a robust integration library. This allows employees to log in once to access all necessary tools, while their access permissions automatically update in real time as their roles or employment status change.
By automating these processes, CloudEagle.ai helps protect data, ensure compliance, reduce IT workload, and ensure that everyone’s access is in line with their roles.
User provisioning and deprovisioning: The tool automates user provisioning and deprovisioning to streamline access management. You can set up auto-provisioning workflows to manage SaaS access efficiently.

When a new user joins, the system automatically suggests relevant apps and configures their access. Conversely, when employees leave, their access is revoked to maintain security.
This automation speeds up the approval and revocation processes. It reduces errors compared to manual methods. Integration with HR systems ensures that all changes are reflected quickly and accurately. It minimizes the risk of unauthorized access and enhances operational efficiency.
Access reviews: CloudEagle.ai makes it easy to manage user permissions. The tool automates the process, so you can quickly check if users have the right access. Regular audits help lower security risks and ensure compliance with regulations.
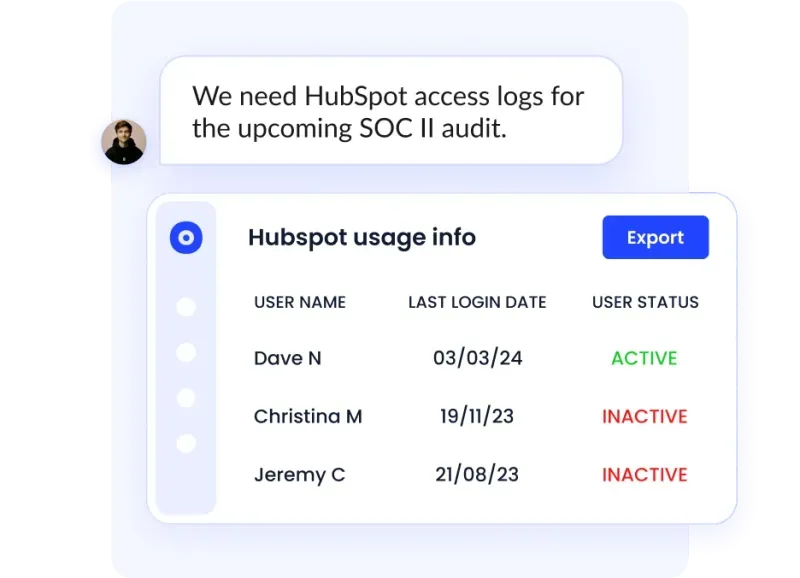
Administrators can easily identify and resolve issues using CloudEagle.ai’s intuitive reporting tools. The integrated dashboard gives a clear overview and helps you respond quickly to potential problems.
Comprehensive reports provide useful insights into compliance and security, making it easier to keep everything under control.
Self-service app catalog: CloudEagle.ai’s self-service application catalog allows users to request and access applications independently. Employees can browse a catalog of available applications and request access to the ones they need without going through IT staff.

After a request is made, administrators receive a notification and review the request. They check if the access aligns with the user’s role and responsibilities. Based on the review, administrators grant or deny access. This ensures that permissions are appropriately assigned and controlled.
This feature speeds up access requests and reduces the burden on IT staff. The customizable catalog allows organizations to control which applications are available for self-service.
Automated approval workflows ensure that all access requests are reviewed according to company policies before they are granted.
Conclusion
Effective entitlement management helps maintain security and regulatory compliance within organizations. It also enhances both operational efficiency and productivity. By implementing a strong CEM strategy, you can minimize the risks of unauthorized access and security breaches.
Clear policies and automated systems ensure compliance with regulations, protect sensitive data, and build trust with stakeholders. Streamlined processes for managing access, such as granting, monitoring, and removing it, reduce administrative work and make handling access requests and issues easier.
Thus, you will need an advanced tool to establish a strong identity and credential management system in your organization.
For advanced access management capabilities, consider CloudEagle.ai, which integrates with over 500 applications, supports SSO and IdPs, and enables robust identity and access management policies.
Schedule a personalized demo to see how CloudEagle.ai can transform your organization's entitlement management processes.
Frequently Asked Questions
- What is a software entitlement?
A software entitlement defines what software a user is authorized to access, including licenses, features, and usage limits. - What is entitlement in cybersecurity?
In cybersecurity, entitlement refers to the specific access rights or privileges assigned to users, apps, or systems. - What is a security entitlement?
A security entitlement is an authorization granted to a user or system to access secured data, files, or applications. - What is a user entitlement?
User entitlement defines what resources, systems, or permissions an individual user is allowed to access. - What is the entitlement system?
An entitlement system manages, tracks, and controls access rights and permissions across apps and systems.

%201.svg)







.avif)




.avif)
.avif)




.png)









