HIPAA Compliance Checklist for 2025

Privileged Access Management is an important aspect of any robust cybersecurity strategy. As cyber threats grow and become harder to combat, protecting privileged accounts has never been more important.
Privileged user accounts have extensive access and control over IT systems and sensitive data.
They typically belong to administrators, IT staff, and executives. Without proper management, these accounts can become a prime target for cyber attackers, leading to data breaches and operational disruptions.
However, effective PAM strategies can mitigate these risks by ensuring that privileged access is carefully controlled. You can also protect your business’s most sensitive resources and maintain regulatory compliance.
In this article, we will discuss what PAM is, its importance in today's threat landscape, the types of privileged accounts, and advanced strategies for mastering access control capabilities.
TL;DR
- Privileged Access Management (PAM) is crucial for cybersecurity, as it controls access to sensitive resources and mitigates risks from unauthorized access, data breaches, and insider threats.
- Understanding different types of privileged accounts—such as local administrative, domain administrative, and emergency accounts—is essential for effective PAM strategies.
- The principle of least privilege, role-based access control, and continuous monitoring are core principles that enhance PAM effectiveness by reducing security risks.
- Common challenges in PAM include lack of visibility into privileged accounts, overprovisioning of privileges, and shared account management, all of which can increase vulnerability.
- Implementing advanced strategies like multi-factor authentication, integrating PAM with Identity and Access Management (IAM), and utilizing AI can significantly improve security and streamline access management processes.
What do you mean by Privileged Access Management?
Privileged Access Management (PAM) is a security framework designed to control, monitor, and protect access to sensitive systems and data. It focuses on managing privileged accounts like IT admins, service accounts, or executives that can make system-level changes or access confidential information.
By enforcing least privilege, session monitoring, and just-in-time access, PAM helps prevent data breaches, insider threats, and unauthorized actions.
It’s a critical part of modern cybersecurity and complements identity and access management (IAM) by securing what users can do once they’re inside the system.
How Privileged Access Management Works?
Privileged Access Management (PAM) works by setting rules and controls around who gets elevated access, how long they have it, and what they can do with it. Instead of permanent, broad privileges, PAM ensures access is limited, monitored, and auditable.
At its core, PAM brings together several moving parts:
- Discovery of Privileged Accounts: PAM tools scan the environment to uncover both human (admins, IT staff) and non-human (service accounts, scripts, APIs) privileged accounts that often go unnoticed.
- Access Restriction with Least Privilege: Users are only given the minimum access needed to perform their tasks. This reduces the damage potential if an account is compromised.
- Role- and Attribute-Based Controls: Instead of granting permissions individually, PAM ties access to roles or attributes. This keeps access aligned with responsibilities and simplifies scaling across teams.
- Continuous Monitoring and Session Oversight: Every privileged session can be tracked and recorded whether that’s a login, configuration change, or database query. This transparency helps enforce privileged access management security and supports compliance.
- Just-in-Time (JIT) Access: Access is temporary and task-based, expiring automatically once the job is done. This removes the risks tied to always-on admin rights.
- Automation Across the Lifecycle: Provisioning and deprovisioning of privileged access is automated, ensuring employees get access when needed, and lose it immediately when roles change or they leave.
- Credential Hardening: Secure vaults, rotating credentials, and multi-factor authentication (MFA) strengthen the protection around privileged accounts, making it harder for attackers to break in.
In short, PAM works by discovering privileged accounts, enforcing strict access policies, monitoring activity, and securing credentials with automation and oversight.
What are the Types of Privileged Accounts?
Remember there are different types of privileged accounts with different access levels. Without understanding the types, you cannot implement effective PAM strategies.
Each type of account serves a specific function and requires distinct security measures. So, you need to pay close attention to them.
Local Administrative Accounts: Used to manage individual workstations and servers, providing full control over local systems.
Domain Administrative Accounts: Provide extensive privileges across the network domain for managing domain resources and configurations.
Break Glass (Emergency) Accounts: Reserved for critical situations to regain control during emergencies when standard access is unavailable.
Active Directory or Domain Service Accounts: Specialized service accounts for managing and maintaining the Active Directory environment.
Service Accounts: Non-human accounts used by applications and services to interact with the operating system and perform automated tasks.
Application Accounts: Used by software applications to access databases, services, and other applications, often requiring specific permissions.
Why is PAM Crucial in Today's Threat Landscape?
As a business owner, you are likely aware that cyber threats are becoming increasingly relentless. Today, these threats predominantly target privileged accounts to exploit the most sensitive data and critical systems.
This is because such accounts provide a gateway for lateral movement within the network, leading to significant data breaches.
Even if they compromise one privileged account, they can access confidential information, disrupt operations, and even hold entire systems hostage for ransom. And, recent high-profile data breaches have motivated hackers more than ever.
So, how can you prevent these threats? The "least privilege" principle, one of the core aspects of PAM, ensures users receive only the minimum level of access necessary to perform their job functions.
When only a minimum number of users can access extensive privileges, the attack surface can be significantly reduced. This will also reduce the risk of accidental or intentional misuse of critical information.
Risks of Uncontrolled Privileged Access
Uncontrolled privileged access is like making your business more vulnerable to attackers. Improper control and management of privileged access will make your business look like an easy prey. To help you understand it better, we will discuss the risks along with the scenario.
1. Increased Attack Surface
Uncontrolled privileged access can greatly enhance your business’s attack surface. Moreover, it will be an opening for the cyber hackers to penetrate into your network.
For instance, imagine an attacker gains access to a single privileged account through a phishing attack or credential theft. Thus, they can move laterally within the network, penetrating the critical systems and data.
This allows the attacker to access sensitive information and disable security controls. They can also install malware and create backdoors for persistent access.
In such cases, it may also lead to widespread data breaches and operational disruptions, which can cause your business serious financial and reputational damage.
2. Accidental Data Breaches
Granting excessive privileges to authorized users increases the risk of accidental data breaches. This is one of the devastating risks of unchecked privileged access.
Let’s consider a scenario where an authorized user with elevated access mistakenly deletes sensitive data. Without proper controls, such actions can cause irreversible damage to critical data and systems.
Apart from that, it can also disrupt business operations, affect regulatory compliance requirements, and affect customer trust. Your business will also face financial problems, including costs associated with data recovery, legal fees, regulatory fines, and loss of business.
3. Difficulty Detecting and Responding to Security Incidents
When you don’t control privileged access, you cannot promptly detect and respond to security incidents. For example, suppose a privileged account is compromised due to weak credentials.
In this scenario, the attacker can operate undetected within the network. They will perform malicious activities, such as exfiltrating data or planting malware, without your notice.
Without comprehensive monitoring and alerting mechanisms in place, security teams may struggle to identify unauthorized access. As a result, you will fail to respond to such situations. The attacker will remain persistent and will cause further damage.
Core Principles of Effective PAM
Effective PAM depends on a few core principles. They are designed to minimize security risks and ensure privileged access is managed and monitored appropriately. Let's look at them.
1. Principle of Least Privilege
The principle of least privilege highlights that users should be granted only the minimum level of access necessary to perform their job functions. By limiting the number of users, you can significantly reduce the risk of unauthorized access to sensitive systems.
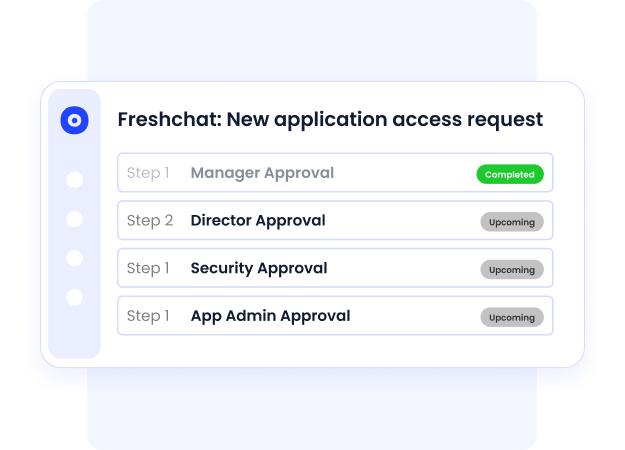
This will undoubtedly help your business minimize potential cyber-attacks. Not to mention, you can also mitigate the damage that could result from compromised accounts.
When you implement this principle, you can regularly review access rights. If you find any discrepancies, you can adjust permissions to align with your employee’s current job responsibilities.
2. Role-Based Access Control (RBAC)
Role-based access control (RBAC) is a method of restricting system access based on the roles of individual users within an organization. RBAC ensures that users receive permissions appropriate to their role rather than getting broad access.

This approach will categorize users into roles with predefined access rights, simplifying access management. You can also implement the principle of least privilege easily to ensure consistent access policies.
RBAC streamlines adding, modifying, and revoking access when employees join, change roles, or leave the organization.
3. Just-in-Time Access
Just-in-time (JIT) access is a security measure that provides users with privileged access only for a certain duration. This is effective when an employee wants to work on specific tasks requiring privileged access.
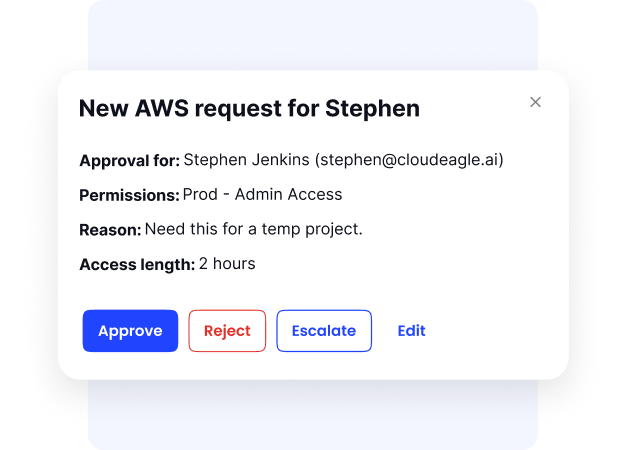
Once the task is completed, you will revoke the access. This will reduce the chances of misuse or attack. JIT can also help you minimize the risk of persistent privileged access being exploited by malicious employees.
JIT access uses automated processes to grant and revoke privileges in real-time based on task needs. This way, it can ensure elevated permissions are used only when necessary.
4. Continuous Monitoring and Auditing
Continuous monitoring and auditing are essential principles of effective Privileged Access Management. They ensure you can track and review all privileged access easily. Hence, you can detect and respond to suspicious or unauthorized actions promptly.

When you identify privileged accounts, you can identify potential security threats in real-time and take immediate action. Moreover, auditing will help you know the records to conduct thorough investigations of security events.
Common Challenges in Privileged Access Management
While effective Privileged Access Management is important, you may often face significant challenges. They can weaken even the best security strategies, leaving critical systems and network devices vulnerable.
1. Lack of Visibility into Privileged Accounts
One of PAM's biggest challenges is the lack of visibility into privileged accounts. Your business may often struggle to maintain an accurate inventory of privileged accounts, making monitoring and managing access difficult.
Without proper visibility, you cannot implement security policies, identify potential risks, and detect unauthorized access. This can lead to unchecked privileges, increasing the risk of security breaches.
2. Overprovisioning of Privileges
This challenge occurs when users are granted more access rights than necessary for their job functions. It often results from a lack of strict access controls or from granting elevated permissions as a convenience.
Overprovisioning violates the principle of least privilege and significantly increases the attack surface. This way, it allows cyber attackers to exploit privileged accounts easily.
So, how can you address this challenge? Simple - just audit and review the access rights regularly to ensure that users have only the privileges they need.
Here's how Alice Park from Remediant used CloudEagle to automate provisioning and deprovisioning, ensuring the users had the right access to applications.
3. Shared Accounts and Passwords
We have seen many businesses sharing accounts and passwords without knowing the consequences. This practice also poses a significant security risk in PAM.
When multiple users share the same account credentials, tracking individual activities and holding users accountable for their actions gets difficult.
Shared accounts can also lead to poor password management practices. To mitigate this challenge, you need to eliminate shared accounts where possible. You must also implement unique credentials for each user, strong password policies, and multifactor authentication.
4. Decentralized Credential Management
Decentralized Credential Management is the process of managing privileged account credentials across various systems. It doesn’t require a centralized oversight mechanism.
But what’s wrong with this approach? For starters, it can lead to inconsistent security practices, which can easily cause credentials to be mishandled or compromised.
Remember that storing privileged credentials in spreadsheets, shared documents, or unsecured locations can be disastrous.
It makes credentials vulnerable to theft and misuse and complicates password rotation and management.
How to Master Access Controls?
Understanding access controls is one thing; mastering them is another. It’s not just about setting permissions; it’s about building a secure, scalable system that adapts to change, prevents misuse, and aligns with how your business operates.
Here’s how to move beyond basics and truly master privileged access control using privileged access management (PAM):
1. Choose the Right Access Control Model
Mastery starts with picking the right model for your environment. Each model offers a different balance of flexibility and security:
- Mandatory Access Control (MAC): Centralized and rigid, ideal for high-security environments like government or healthcare.
- Discretionary Access Control (DAC): Resource owners control access, more flexible but risky.
- Role-Based Access Control (RBAC): The most common is users get access based on their job role. Easier to manage at scale.
- Attribute-Based Access Control (ABAC): Dynamic and granular, access depends on user attributes, environment, and actions.
→ Pro tip: RBAC + ABAC is often the sweet spot for modern SaaS and hybrid-cloud businesses.
2. Apply the Principle of Least Privilege (PoLP)
This is your foundation. No user should have more access than they need, and certainly not forever.
- Grant the minimum permissions needed to perform a task
- Remove default admin rights across departments
- Regularly review and re-align access with current roles and responsibilities
→ This isn’t a one-time setup. It’s a discipline that matures with automation.
3. Layer Security with Multi-Factor Authentication (MFA)
Even well-configured access controls are vulnerable without identity verification.
- Enforce MFA on all privileged accounts
- Use token-based, app-based, or biometric MFA
- Pair with session tracking for real-time visibility
→ MFA helps protect against stolen credentials and social engineering attacks.
4. Conduct Regular Access Reviews and Certifications
Mastering access control means making access reviewable and accountable, not static.
- Schedule quarterly access reviews for high-privilege roles
- Audit usage: if access isn’t being used, revoke it
- Use certification workflows to let managers approve or deny access renewals
→ With CloudEagle, you can automate this end-to-end and never miss a review.
5. Automate User Provisioning and Deprovisioning
Manual access management is where mistakes happen. Automating it means fewer gaps and less risk.
- Integrate access workflows with HRMS or ITSM systems
- Auto-provision access when someone joins or switches roles
- Auto-deprovision access on offboarding, no delays or shadow users
→ This is where CloudEagle’s provisioning engine shines, syncing access with the user's lifecycle.
6. Embrace Zero Trust Architecture
To master access, you must stop assuming trust based on location or login.
- Never trust, always verify, even internal users
- Use Just-in-Time (JIT) access to eliminate always-on privileges
- Apply microsegmentation to limit lateral movement
→ PAM and Zero Trust go hand in hand. Together, they make access dynamic and conditional.
7. Monitor, Analyze, and Adapt Continuously
No access control strategy is ever complete, threats evolve, and so must your policies.
- Monitor session activity, behavior anomalies, and policy violations
- Set up real-time alerts for unusual privilege escalations or access attempts
- Use AI/ML tools to detect patterns humans might miss
→ With CloudEagle, teams get centralized visibility across all apps, users, and access plus proactive alerts before things go wrong.
Mastering access control isn’t about adding more rules; it’s about applying the right ones intelligently, consistently, and automatically.
And with CloudEagle.ai, mastering it doesn’t have to be manual.
Benefits of Mastering Access Controls with PAM
Effective PAM offers numerous benefits that can boost your business’s security, compliance, and operational efficiency.
Controlling access with PAM will undoubtedly help your business protect multi-cloud environments from cyber threats and ensure compliance.
1. Enhanced Security Posture and Reduced Cyber Risks
Privileged Access Management can reduce your business’s attack and prevent authorized access. Thanks to the principle of least privilege, PAM ensures users only have the access necessary for their roles.
So, what’s the benefit? It can reduce the potential for misuse or exploitation of privileged accounts.
Additionally, continuous monitoring and auditing of privileged activities can help you detect and respond to suspicious behavior in real-time. This way, you can identify the serious threats before they become large.
Statistics and Reports
- According to a report by CyberArk, organizations implementing PAM can reduce the risk of a major breach by 50%.
- A study by Forrester Research found that organizations using PAM experienced an 80% reduction in the likelihood of credential theft.
These stats showcase the effectiveness of PAM in reducing cyber attacks and protecting sensitive data. If you want to boost the overall security protocols, you must master access control with PAM.
2. Improved Compliance with Data Security Regulations
PAM can help you follow various data privacy regulations, such as GDPR, HIPAA, and PCI DSS. They mandate strong access controls to protect sensitive information.
PAM provides granular control over who can access specific data. It also maintains detailed audit trails of all privileged activities. As a result, it ensures your organization meets these regulatory requirements.
As PAM can address these compliance requirements, you can avoid hefty fines and reputational damage associated with non-compliance.
Furthermore, it can also showcase your business’s commitment to data protection.
3. Increased Operational Efficiency and Productivity
PAM can streamline access management processes and reduce administrative overload, improving your business's overall operational efficiency.
Automated workflows and self-service access provisioning enable quicker and more accurate assignment of privileges. This will enable IT teams to focus more on the strategic tasks. You can save time and reduce errors in access provisioning.
Benefits of Automated Workflows and Self-Service Access Provisioning
- You can automate access requests and approval processes
- Ensures users receive the correct permissions based on predefined roles and policies
- With proper access governance, you can ensure your employees perform their tasks without unnecessary delays
How CloudEagle.ai Helps with Privileged Access Management?
Managing privileged access manually is a recipe for risk—shared passwords, orphaned accounts, and delays in revoking access can all expose your business. CloudEagle turns that chaos into control by automating and centralizing how you manage elevated access across your SaaS stack.
Here’s how CloudEagle makes privileged access simple and secure:
- Centralized dashboard for full visibility: No more spreadsheets or scattered logs. CloudEagle gives IT and security teams a single view of all users, roles, and privileged accounts across hundreds of SaaS applications.
- Automated lifecycle management: Provisioning and deprovisioning are handled automatically. Employees get the right access on day one, and access is revoked the moment they leave, closing the door on orphaned or lingering accounts.
- Just-in-Time (JIT) & Time-Bound Access: Instead of always-on admin rights, CloudEagle enforces temporary, task-based access that expires automatically. This keeps privileges lean and reduces the attack surface.
- Role-Based Access Control (RBAC): Permissions are tied to roles, not individuals. Finance users only see finance tools, DevOps gets deployment systems, and no one has more than they need.
- Continuous monitoring & alerts: Every privileged action is logged and auditable. CloudEagle’s monitoring flags unusual access patterns instantly, helping you catch threats before they turn into incidents.
- Compliance made easy: Whether it’s SOC 2, HIPAA, or GDPR, CloudEagle generates ready-to-use audit trails and reports, simplifying compliance reviews and reducing audit prep from weeks to hours.
In short, CloudEagle doesn’t just help you “manage” privileged access; it automates it, enforces least privilege at scale, and gives you the visibility to prevent breaches before they happen.
What is the difference between IAM and Pam?
Remember that PAM and IAM are not the same. While they are crucial aspects of cybersecurity, there are significant differences.
Here’s a table that will help you understand the differences between these two.

Conclusion
Cyber threats are continuously growing, causing hackers to become desperate to access sensitive data. Recently, cyber insurers have urged their clients and prospects to implement privileged access security.
This includes certain Privileged Access Management such as user monitoring and admin removal. However, the best way to determine the effectiveness of PAM is by auditing the privileged risks.
But, manual access control will take a significant amount of time and effort. This is why you should consider automation, especially automated user provisioning and deprovisioning. With CloudEagle, you can manage access easily and protect your business’s sensitive data.
With our identity and access management features, you can manage, audit, and secure access to all your business applications. You can also track the access properly.
Sounds excellent, right? If you want us to automate the application access, make sure you schedule a demo with us today!
FAQ
1. What is privileged access management in cybersecurity?
Privileged Access Management (PAM) is a security practice that controls, monitors, and secures accounts with elevated permissions. It prevents unauthorized access, limits insider threats, and protects sensitive systems and data.
2. What is the PAM methodology?
The PAM methodology involves discovering privileged accounts, enforcing least privilege, using just-in-time access, monitoring sessions, automating provisioning, and securing credentials with MFA and vaulting to reduce risks and ensure compliance.
3. What are the indications of an incident fall into two categories cyber?
The indications of an incident fall into two categories: Indicators of Compromise (IoCs), like malware or unusual logins, and Indicators of Attack (IoAs), like privilege escalation or lateral movement. Monitoring both helps detect and respond quickly.
4. Which of the following certifications would satisfy IAM level 2 and level 3?
IAM Level 2 and Level 3 can be satisfied by certifications such as CompTIA Security+, CISSP, and Certified Identity and Access Manager (CIAM). These validate skills in identity management, access control, and advanced cybersecurity practices.

%201.svg)







.avif)




.avif)
.avif)




.png)









