HIPAA Compliance Checklist for 2025

SaaS apps' ease of purchase and a lack of application visibility have made shadow IT more prevalent in today’s organizations. Moreover, users' active involvement in shadow IT is influenced by their lack of understanding of the associated risks.
Approximately 65% of SaaS applications in organizations are unsanctioned, used without IT approval, making shadow IT a pervasive issue across industries.
It poses a significant security threat to your SaaS stack, as they are not subject to the same risk assessment and vetting process as approved software.
If your SaaS ecosystem is plagued by shadow IT, then this article is just what you need. Learn about shadow IT risks and clever ways to mitigate them in this quick read.
Let us talk about this in detail.
TL;DR
- Shadow IT refers to software or cloud apps used by employees without IT approval, creating hidden risks and a lack of control over the organization’s tech environment.
- It leads to security vulnerabilities because unauthorized apps often bypass security vetting, increasing the chances of data breaches and compliance violations.
- Shadow IT causes data loss risks when sensitive information is stored in unapproved apps, which may not follow company policies or be accessible if employees leave.
- It results in untracked expenses and duplicate SaaS subscriptions, complicating budget management and increasing overall IT costs.
- Mitigation requires 100% visibility, centralized procurement, regular audits, and employee education, supported by SaaS management platforms like CloudEagle.ai to detect, control, and optimize SaaS usage securely.
What is Shadow IT?
Shadow IT refers to the use of IT systems, software, or services within an organization without the explicit approval or oversight of the IT department. These unauthorized tools or solutions are often adopted by employees or teams to meet specific needs or improve productivity, bypassing formal IT processes.
This can create security risks and issues since these applications often do not go through the same vetting and security processes as the organization's approved software.
One of the most common occurrences of shadow IT is the use of cloud services. Employees may use cloud-based storage or collaboration tools like Google Drive, Dropbox, or Slack without the IT department's knowledge or approval.
They may also use cloud-based applications or software as a service (SaaS) solutions such as Salesforce, HubSpot, or Trello. While cloud-based tools and services can offer many benefits for businesses, using them without proper vetting and security measures can create significant risks for organizations.
Six Common Shadow IT Risks You Should Be Aware Of
1. Lack Of Control On Applications
There is an urban folklore, “ You cannot protect what you can’t see.” This rings true for shadow IT as it pertains to the apps outside the IT team's purview.
As a result, teams cannot effectively track and control shadow IT. This means there's a greater chance of security issues, errors, and non-compliance within the system.
2. Loss Of Sensitive Customer And Business Data
Another issue associated with shadow IT is that information or data saved in personal accounts may not be available to other company members. If an employee quits or gets fired, they might still retain access to those resources saved in the cloud while the business loses them.
It's also essential to note that shadow IT is not bound by corporate rules and regulations. As a result, the data saved on a cloud server may not be secured, archived, or encrypted according to company policies.
3. Increased Expenses Due To Unverified Spending
Shadow IT can increase SaaS expenses for an organization due to unverified spending on unauthorized software, applications, and services. Employees may subscribe to cloud services or purchase software without approval from the IT department or the organization's budgetary department.
Without proper oversight, unverified spending on shadow IT can result in duplicate expenses across departments, conflicting licenses and subscriptions, and a lack of centralized management of IT resources.
Additionally, IT teams may face difficulties in tracking and managing shadow IT expenses, resulting in difficulties reconciling invoices and managing budgets effectively.

4. Security Breaches
Dealing with cybersecurity breaches is arguably the most pressing IT operations challenge today. As shadow IT practices may involve using unauthorized third-party vendor apps, this can lead to security vulnerabilities such as firewall breaches.
Nearly half of cyberattacks originate from shadow IT, with the average cost of a breach related to unauthorized apps exceeding $4.2 million.
Moreover, internal shadow IT activities may compromise existing security software, such as virus detection, or security equipment, like intrusion detection systems.
5. Non-compliance With Industry Regulations
Organizations are subjected to security audits and regulations to ensure that the software is capable of securing sensitive customer data. Shadow IT practices may inadvertently lead to issues like security breaches, system failures, and data thefts.
These issues will lead to non-compliance with security standards and have a detrimental impact on the organizations. Most third-party vendors falsify compliance certifications, and shadow IT will open the doors for those vulnerable vendors to exist in your system, leading to security risks and non-compliance.
6. Automated Renewals
Automated renewals of unauthorized subscriptions and services in shadow IT will create challenges for the finance team.
It’ll lead to continued billing of unauthorized services, making it difficult to track costs effectively as there will be no visibility, leading to increased SaaS expenses and related security risks.
How to Find Shadow IT Risks?
Cloud Access Security Broker (CASB): CASB solutions provide visibility and control over cloud applications used within an organization. They monitor cloud service usage, detect unauthorized apps, and enforce security policies to reduce shadow IT risks.
Manual Inventory via Spreadsheet: Some organizations track applications and devices manually using spreadsheets. While simple, this approach is prone to errors and often incomplete, making it less effective for identifying shadow IT comprehensively.
Single Sign-On Platforms (SSO): SSO platforms centralize user authentication across multiple applications. By analyzing SSO logs, IT teams can identify which apps employees are accessing, helping uncover unauthorized or shadow IT usage.
Financial Discovery and Analysis: Reviewing procurement records, expense reports, and invoices can reveal unapproved software purchases or subscriptions. Financial analysis helps detect shadow IT by highlighting spending outside official IT budgets.
What are the Reasons Behind Shadow IT Usage?
User Convenience and Speed: Employees often turn to shadow IT to quickly access tools they feel improve productivity, bypassing slow or restrictive IT approval processes.
Inadequate Official Tools: When sanctioned IT solutions don’t meet user needs or lack certain features, staff may seek alternative apps on their own.
Lack of Awareness: Users may not understand the security risks or compliance implications of using unauthorized software.
Remote and Hybrid Work: Distributed workforces increase the likelihood of employees adopting unsanctioned cloud apps for collaboration and file sharing.
Innovation and Flexibility: Departments sometimes adopt new technologies independently to innovate or solve specific problems without waiting for centralized IT support.
How to Mitigate the Risks of Shadow IT?
Here are a few tips that can help mitigate the risks of shadow IT;
100% Visibility and Control
To mitigate the risks of shadow IT, enterprises must have complete visibility of the apps purchased and used by employees. Implement a SaaS management platform that ensures a centralized system for purchasing and provisioning IT resources.

This will help ensure complete application visibility of the SaaS stack and ensure all resources are acquired through approved channels. Thus reducing the likelihood of unauthorized purchases.
Improve Compliance
Businesses must establish clear policies, procedures, and guidelines for IT practices and ensure adherence to regulatory needs. This can be achieved by implementing compliance frameworks and SaaS management software which provide a framework for managing security risks.
Organizations should also regularly educate and train their employees on IT policies and guidelines to ensure they know the risks associated with shadow IT and the consequences of non-compliance.
Create A Centralized Procurement Process
Businesses should build a centralized procurement process to ensure all purchases are authorized and comply with organizational policies.

This can be achieved by implementing a SaaS procurement platform that streamlines the process for purchasing IT applications, including who is authorized to purchase them, the process for approving purchases, and how purchases are tracked.
Perform Regular Audits
Organizations should conduct regular audits to identify any unauthorized IT activities and take suitable actions to combat the risks. This can be achieved through the use of SaaS management software which provides governance and management of enterprise IT as well as audits.
These audits will reveal the duplicate applications existing in your SaaS ecosystem due to shadow IT, so you can take counteractive measures to eliminate such applications.
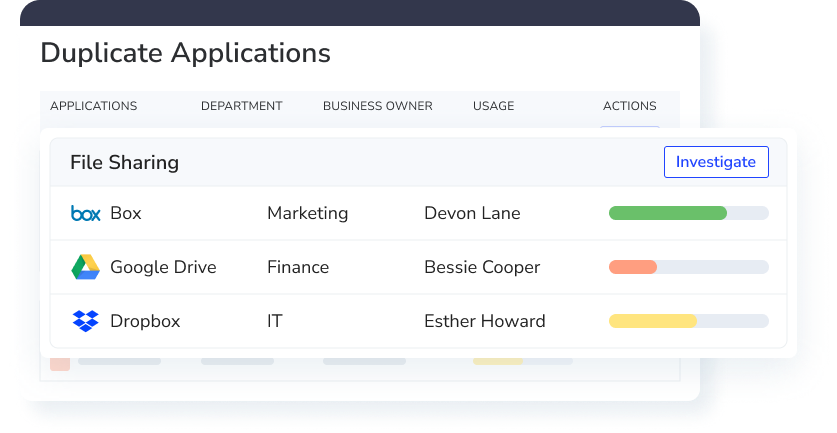
A SaaS spend management platform can help you audit your spending on SaaS applications. You can use the platform to detect anomalies within your stack, as it integrates with your financial systems.
You can use a SaaS spend management platform to identify paid and free tools and optimize them to keep your tech stack secure.
Communicate With The Team And Consider Their Needs
Organizations should communicate with their employees and consider their needs to ensure they have access to the tools and resources needed to perform their jobs effectively while adhering to organizational IT policies and guidelines.
This can be achieved through regular IT policy training and by providing employees with the tools and resources to perform their jobs effectively. Additionally, organizations should establish a process for employees to request new tools and resources that are not currently available, which IT administrators can review and approve.
Eliminating the Risks of Shadow IT with CloudEagle.ai
CloudEagle.ai is a SaaS management platform that can help organizations eliminate the dangers of shadow IT as it is equipped with features like,
Comprehensive Application Discovery and Visibility
CloudEagle.ai automatically discovers all SaaS applications in your environment, including unauthorized and shadow IT apps, by integrating with SSO, HRIS, finance, and network systems.

With over 500+ direct integrations, it provides a unified, bird’s-eye view of your entire SaaS stack, revealing hidden apps that IT teams might not know about.
Proactive alerts notify admins immediately when an unsanctioned app enters your ecosystem, enabling early intervention before risks escalate.
Shadow IT Detection and User Engagement
The platform tracks app usage and spending, including purchases made via corporate credit cards, to identify shadow IT sources.
IT teams can send automated inquiries to users who adopt unsanctioned apps, helping understand their needs and deciding whether to approve, consolidate, or eliminate these apps.

Duplicate and redundant applications are flagged automatically, helping reduce unnecessary costs and complexity.
Discover this inspiring success story of how Rec Room gained complete visibility into the free apps used by its teams with CloudEagle.ai.
Centralized SaaS Procurement and Governance
CloudEagle.ai centralizes the procurement process, ensuring all SaaS purchases are authorized, compliant, and cost-effective.

Contract management features enable categorization, tagging, and tracking of renewal dates, making audits and vendor negotiations easier and more efficient.
Dynamic filters and detailed reports provide insights into vendor spend, departmental usage, and license allocation.
Cost Optimization and License Management
By identifying underused or inactive licenses, CloudEagle.ai helps reclaim and reallocate SaaS licenses, reducing wasted spend. Organizations typically save 10-30% on software costs by eliminating shadow IT and optimizing license usage.

Benchmarking data helps negotiate better pricing with vendors based on actual usage and market standards.
User-Friendly Interface and Workflow Automation
The no-code, drag-and-drop workflows allow IT, security, and procurement teams to automate onboarding, offboarding, access reviews, and license reclamation.
Slack-enabled workflows enable users and admins to request, approve, or comment on app access directly within familiar communication tools, increasing adoption and reducing friction.
Automated alerts and reports keep stakeholders informed and help maintain continuous compliance.
Enhanced Security and Compliance
CloudEagle.ai ensures only authorized and compliant applications are in use, reducing attack surfaces created by shadow IT.

It supports compliance with standards like SOC 2, ISO 27001, GDPR, and HIPAA by providing audit trails, access reviews, and risk scoring of SaaS apps.
Continuous monitoring and risk assessment help prioritize remediation efforts on high-risk applications.
Conclusion
Shadow IT poses a significant challenge for organizations, and taking steps to mitigate its risks is imperative.
Organizations can reduce shadow IT risks by implementing the above-mentioned measures, ensuring 100% application visibility, improving compliance, centralizing procurement processes, creating a transparent culture, and communicating with the team.
Cloud management software like CloudEagle.ai can assist IT teams in managing SaaS applications and optimizing their SaaS stack while mitigating Shadow IT risks. Organizations can protect their data, systems, and reputation by proactively addressing Shadow IT.
Are you already aware of the risks of shadow IT and looking for a way to minimize it?
Schedule a demo with CloudEagle.ai and discover how to secure your SaaS environment while optimizing costs and compliance.
FAQs
1. Explain the concept of shadow it and its risk?
Shadow IT is the use of unauthorized software or devices within an organization, which can lead to security risks, data loss, compliance issues, and increased costs. Proper monitoring and management are essential to minimize these risks.
2. What is shadow spending?
Shadow spending refers to unauthorized or unapproved purchases made by employees—often using corporate credit cards—without going through the official procurement process, leading to hidden costs and budget control issues.
3. What is shadow usage?
Shadow usage is the use of software, applications, or IT resources within an organization without the knowledge or approval of the IT department, often creating security and compliance risks.
4. What is shadow procurement?
Shadow procurement involves acquiring goods or services, especially IT-related, outside of formal procurement channels and policies, bypassing approval workflows and financial oversight.
5. What is shadow IT monitoring?
Shadow IT monitoring is the ongoing process of discovering, tracking, and managing unauthorized IT assets and applications used within an organization to mitigate associated security, compliance, and cost risks.

%201.svg)







.avif)




.avif)
.avif)




.png)









