HIPAA Compliance Checklist for 2025

What if half your workforce still had access to systems they no longer need? A report by CloudEagle.ai shows 1 in 2 employees retain unnecessary access after role or project changes, creating hidden risks that slip past routine controls.
That’s where access recertification comes in, helping you validate and clean up access before it turns into a breach. This article explains what it is, why it matters, how the process works, and the challenges to watch for, so you can keep access clean, compliant, and secure.
TL;DR
- Access recertification is the periodic review of user entitlements to prevent privilege creep, insider threats, and compliance failures.
- It enforces least privilege, reduces risks, and ensures audit readiness with proper documentation.
- Types include user, account, and access recertification, with models ranging from periodic to dynamic real-time checks.
- The recertification process involves identifying entitlements, assigning reviewers, approving/revoking access, remediating issues, and maintaining audit logs.
- CloudEagle.ai automates recertification, streamlines audits, optimizes licenses, and reduces manual effort, helping enterprises secure data while saving costs.
What is Access Recertification?
Access recertification is the practice of periodically reviewing user access rights to confirm they are still valid, necessary, and aligned with organizational policies. In simple terms, it’s a security checkpoint, verifying that employees, contractors, or partners only hold the permissions they need to perform their current roles.
Also referred to as user access certification or access and entitlement certifications, the process enforces the principle of least privilege, reducing the risks of insider threats, privilege creep, or accidental data exposure.
When you define recertification in a compliance context, it means more than just cleaning up outdated accounts; it’s proof to regulators and auditors that your organization actively manages who has access, when, and why.
Put differently: if regular user access review checklists show you “who has access,” recertification ensures you validate and, if needed, revoke it, closing security gaps before they can be exploited.
Why Access Recertification Matters?
Access risks rarely appear overnight; they build up slowly through outdated permissions, unchecked role changes, and forgotten accounts.
Access recertification is the safeguard that keeps those risks in check, ensuring your organization stays secure, compliant, and audit-ready.
Enforces the Principle of Least Privilege
Over time, employees collect permissions they no longer need – what’s known as privilege creep.
By conducting regular recertification, managers validate each entitlement and revoke excess rights, reinforcing role-based access control (RBAC) and the principle of least privilege. This ensures people only access what’s essential for their jobs, nothing more.
Improves Compliance with Regulatory Standards
From SOX to HIPAA, GDPR, and ISO 27001, most regulatory frameworks require periodic user access certification.
Access recertification provides the evidence, such as detailed logs, audit trails, and approvals, that proves you’ve aligned with these standards. Without it, compliance gaps can trigger penalties and damage trust.
Reduces the Risk of Insider Threats and Privilege Creep
Not all breaches come from hackers.
Research shows 1 in 2 employees retain access they don’t need after role changes.
These lingering entitlements create perfect conditions for insider threats, whether intentional or accidental. Recertification eliminates that excess, shutting down backdoors before they can be exploited.
Enhances Audit Readiness and Reporting Accuracy
Auditors want more than policy statements; they want proof.
By maintaining clear records through the recertification process, organizations demonstrate accountability, reduce audit preparation time, and provide accurate reports on access and entitlement certifications.
Instead of scrambling during audit season, you’ll already have the evidence in place.
Types of Access Recertification
Not all access recertification efforts look the same.
Depending on the scope and method, organizations adopt different approaches to validate access rights. Two of the most common distinctions are by target (user, account, or access) and by approach (static vs. dynamic).
User vs. Account vs. Access recertification
- User Recertification: Reviews all roles, accounts, and group memberships tied to a single individual. Think of it as a complete check-up of everything one user can access.
- Account Recertification: Focuses on specific accounts across services or applications, ensuring they’re still active, valid, and tied to the right owner. This often uncovers orphan accounts left behind after employees exit.
- Access Recertification: Targets particular entitlements or permissions, such as admin rights in a CRM to confirm whether they’re still needed. This form is especially critical in high-risk or compliance-heavy systems.
Static (RBAC) vs. Dynamic (ABAC) Approaches
- Static / Role-Based Access Control (RBAC): Traditional recertification uses predefined roles. Managers periodically check whether a user’s role-based permissions still apply. It’s effective but only captures a snapshot in time, meaning changes between reviews may slip through.
- Dynamic / Attribute-Based Access Control (ABAC): Instead of waiting for quarterly or annual reviews, ABAC evaluates access in real time based on attributes like location, device, or role status. This “dynamic recertification” adapts instantly to changes, reducing the window of unnecessary access.
When you combine user access certification with either RBAC or ABAC models, organizations can balance compliance requirements with security agility, closing the gap between outdated permissions and real-world threats
How Often Should Access Recertification Be Done?
There’s no one-size-fits-all answer to access reviews; the right frequency depends on your risk profile, regulatory environment, and business needs.
The key is making sure your recertification process is not checking boxes in the checklist, but is a reliable safeguard against privilege creep and compliance gaps.
Periodic Recertification
Most organizations conduct access reviews on a quarterly or annual basis.
This aligns with regulatory requirements such as SOX, HIPAA, or GDPR, which expect documented user access certification at regular intervals. Periodic access reviews help ensure that excessive permissions are trimmed back on schedule.
Event-Based Recertification
Some changes can’t wait until the next cycle.
New hires, promotions, exits, and role transfers are high-risk events that demand immediate access and entitlement certifications. Event-based reviews ensure access is revoked or adjusted before old rights create vulnerabilities.
Continuous or Dynamic Models
Forward-looking teams adopt continuous monitoring through attribute-based access control (ABAC).
Unlike static schedules, this model validates access in real time, adapting instantly to changes like job moves or location shifts. While not every organization is ready for this approach, dynamic recertification is emerging as a best practice for minimizing gaps between reviews.
The Process of Access Recertification
A successful recertification process follows a repeatable, structured workflow. Each step ensures user permissions remain aligned with roles, policies, and compliance requirements.
Step 1: Identify Access Entitlements and Users
Start by mapping every account, role, and entitlement across your systems.
This includes employees, contractors, and external partners. Comprehensive discovery is critical; missing accounts can leave you exposed.
Step 2: Assign Reviewers Based on Roles or Ownership
Managers, application owners, or data owners should validate access for their teams.
This ensures reviews aren’t done in isolation but by people who understand the business context.
Step 3: Collect Approval or Revocation Decisions
During user access certification, reviewers must decide whether permissions are still justified.
This eliminates privilege creep by revoking rights that are no longer needed.
Step 4: Remediate Access Based on Reviewer Input
Approvals and revocations aren’t enough; changes must be executed quickly.
Automated remediation prevents delays, reduces errors, and minimizes risks from dormant or excessive accounts.
Step 5: Maintain Logs and Generate Audit Reports
Finally, document every decision.
Detailed logs and reports provide proof of compliance, support audits, and strengthen accountability in access and entitlement certifications.
What are the Challenges of Access Recertification?
Even though access recertification is critical for security and compliance, carrying it out effectively isn’t always easy.
Here are some of the most common hurdles organizations face:
1. Review fatigue and rubber-stamping
Managers are often flooded with access requests to approve. When the volume is too high, they may approve everything without proper review just to move faster.
This leads to outdated or unnecessary access slipping through. The fix is to stagger reviews, automate where possible, and provide managers with clear, prioritized tasks.
2. Lack of context for reviewers
Without details like usage history or role changes, reviewers are left guessing whether access is still needed. This makes reviews inconsistent and increases the risk of privilege creep.
Providing reviewers with contextual information, such as last login date or project assignment, helps them make informed decisions.
3. Manual and time-consuming processes
Spreadsheets and email approvals are still common, but they don’t scale.
Manual reviews are slow, prone to error, and can drag on past audit deadlines. Automating parts of the recertification process reduces the workload and ensures accuracy.
4. Complex organizational structures
Access recertification becomes especially difficult in enterprises with multiple departments, layers of hierarchy, or global teams.
Defining roles and responsibilities takes longer, often delaying reviews. To handle this, organizations should establish clear recertification policies and maintain close collaboration with departmental stakeholders.
5. Siloed systems and poor integration
When access data is spread across disconnected SaaS apps, on-prem systems, and legacy platforms, it’s hard to see the complete picture.
This lack of integration creates blind spots and makes certification reports unreliable. Centralizing entitlement data through IAM or IGA solutions helps overcome this challenge.
6. Insufficient stakeholder buy-in
Recertification isn’t just IT’s job; it requires commitment from managers, auditors, and business leaders.
Without buy-in, reviews are rushed or skipped altogether. Awareness training and executive sponsorship can help drive accountability.
7. Privilege creep and compliance pressure
Over time, employees accumulate more permissions than they need.
If not revoked, these privileges increase insider threat risks and raise red flags during audits. Regulatory frameworks like SOX, HIPAA, and GDPR require strict user access certification, making it critical to track and regularly revoke excessive rights.
How CloudEagle.ai’s Access Management Feature Help Enterprises?
Manual reviews, spreadsheets, and siloed systems make access recertification harder than it should be. That’s where CloudEagle.ai steps in, turning a painful, error-prone task into a streamlined, automated process that strengthens security while cutting costs.
Enhanced Security
CloudEagle automates provisioning and deprovisioning, ensuring new users get the right access from day one and former employees lose their entitlements immediately.

Real-time monitoring highlights unusual patterns, while privileged accounts are tightly controlled to reduce insider risks.
Streamlined Compliance & Audits
Instead of scrambling at audit time, enterprises can rely on CloudEagle’s user access certification capabilities.

Automated app acess reviews and detailed logs provide auditors with clear, trustworthy evidence of compliance with SOC 2, ISO 27001, HIPAA, and GDPR.
Increased Efficiency & Productivity
A unified dashboard gives full visibility into users, roles, and entitlements across SaaS apps, no more jumping between systems.
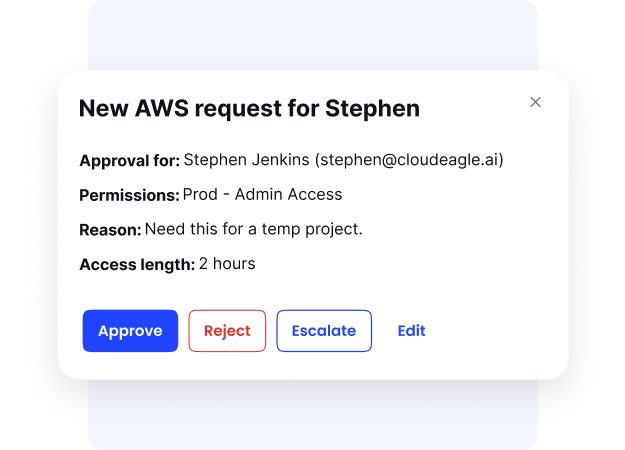
With automated workflows and just-in-time access, approvals move faster, and temporary users like contractors get the right level of access without lingering permissions.
Cost Optimization
Unused licenses and duplicate entitlements drain budgets. CloudEagle identifies underutilized apps, reallocates licenses, and eliminates waste.

The result? Lower spend on SaaS while reducing the manual workload for IT and procurement teams.

By combining automation, visibility, and cost control, CloudEagle ensures access recertification is no longer a compliance checkbox; it becomes a driver of security, efficiency, and savings.
Make Access Reviews Work for You
Regular access recertification reduces risk, stops privilege creep, and proves compliance without slowing down your business. With the right process, you stay secure and audit-ready year-round.
CloudEagle.ai makes that process easier. From automating reviews to optimizing licenses, it helps you cut manual effort, tighten security, and save costs – all while staying compliant.
Ready to simplify access recertification? Book a demo today.
FAQs
1. What does access recertification mean?
Access recertification is the periodic review of user access rights to ensure they’re still valid, necessary, and compliant with policies. It helps reduce privilege creep, prevent unauthorized access, and prove compliance during audits.
2. What is the difference between access review and access recertification?
Access review checks actual user permissions across systems to confirm compliance. Access recertification validates previously approved access requests to ensure they’re still relevant. Both complement each other in enforcing least-privilege and security.
3. What is recertification in IAM?
In Identity and Access Management (IAM), recertification is the process of verifying that users’ access to apps, systems, and data is appropriate. It strengthens security, supports compliance, and ensures permissions align with job roles.
4. What is access certification in IAM?
Access certification in IAM is the formal process of managers or system owners attesting to whether user access rights are still required. It prevents unauthorized access, ensures least-privilege, and documents evidence for compliance audits.
5. What is user account recertification?
User account recertification is the periodic validation of individual user accounts to confirm that access entitlements match current roles. It helps revoke outdated rights, remove dormant accounts, and keep systems secure and audit-ready.
.avif)
%201.svg)







.avif)




.avif)
.avif)




.png)








