Today’s threat landscape is evolving rapidly, with cybercriminals exploiting identity-based vulnerabilities as the primary attack vector. Compromised credentials, excessive privileges, and lack of real-time access controls have rendered traditional Identity and Access Management ineffective in mitigating modern security threats.
This blog explores the shortcomings of traditional Identity and Access Management, introduces Access Governance as the future-ready approach, and provides a step-by-step guide for CIOs to implement an effective access governance strategy.
Additionally, we will discuss how CloudEagle.ai plays a crucial role in enhancing Access Governance by leveraging AI-driven automation, real-time monitoring, and adaptive security controls
.
1. TL;DR
- Traditional IAM is outdated – It lacks scalability, automation, and risk-based controls needed for modern cloud-first environments.
- Access Governance is the future – It enhances visibility, enforces least privilege, and automates compliance.
- AI & automation are essential – Machine learning helps detect risky access behaviors and enforce real-time security policies.
- CIOs must adopt a Zero Trust approach – Implementing Just-in-Time (JIT) access, continuous monitoring, and dynamic controls strengthens security.
- CloudEagle.ai simplifies Access Governance – It offers AI-driven automation, real-time compliance, and seamless multi-cloud integration.
2. The Shortcomings of Traditional IAM

Many organizations still rely on on-premises Identity and Access Management solutions, which are not designed for modern cloud-first environments. These legacy systems lack:
- Scalability to handle access across multi-cloud platforms.
- Flexibility to integrate with the growing ecosystem of SaaS applications.
- Automation to enforce real-time access policies dynamically.
Hybrid IT environments require seamless access control across AWS, Azure, Google Cloud, and SaaS platforms like Salesforce, ServiceNow, and Workday. Traditional IAM solutions struggle to unify and access policies across these diverse infrastructures, leading to security gaps and operational inefficiencies.
Furthermore, legacy Identity and Access Management systems often require extensive manual configurations and scripting to function across different environments, increasing operational complexity.
IT teams must continuously patch, update, and maintain these systems, which becomes increasingly difficult as businesses scale their operations globally.
The high cost of maintaining legacy Identity and Access Management solutions, combined with their inability to support emerging technologies like zero trust security models and AI-driven access controls, makes them a liability rather than an asset.
3. Static Role-Based Access Control (RBAC) Pitfalls
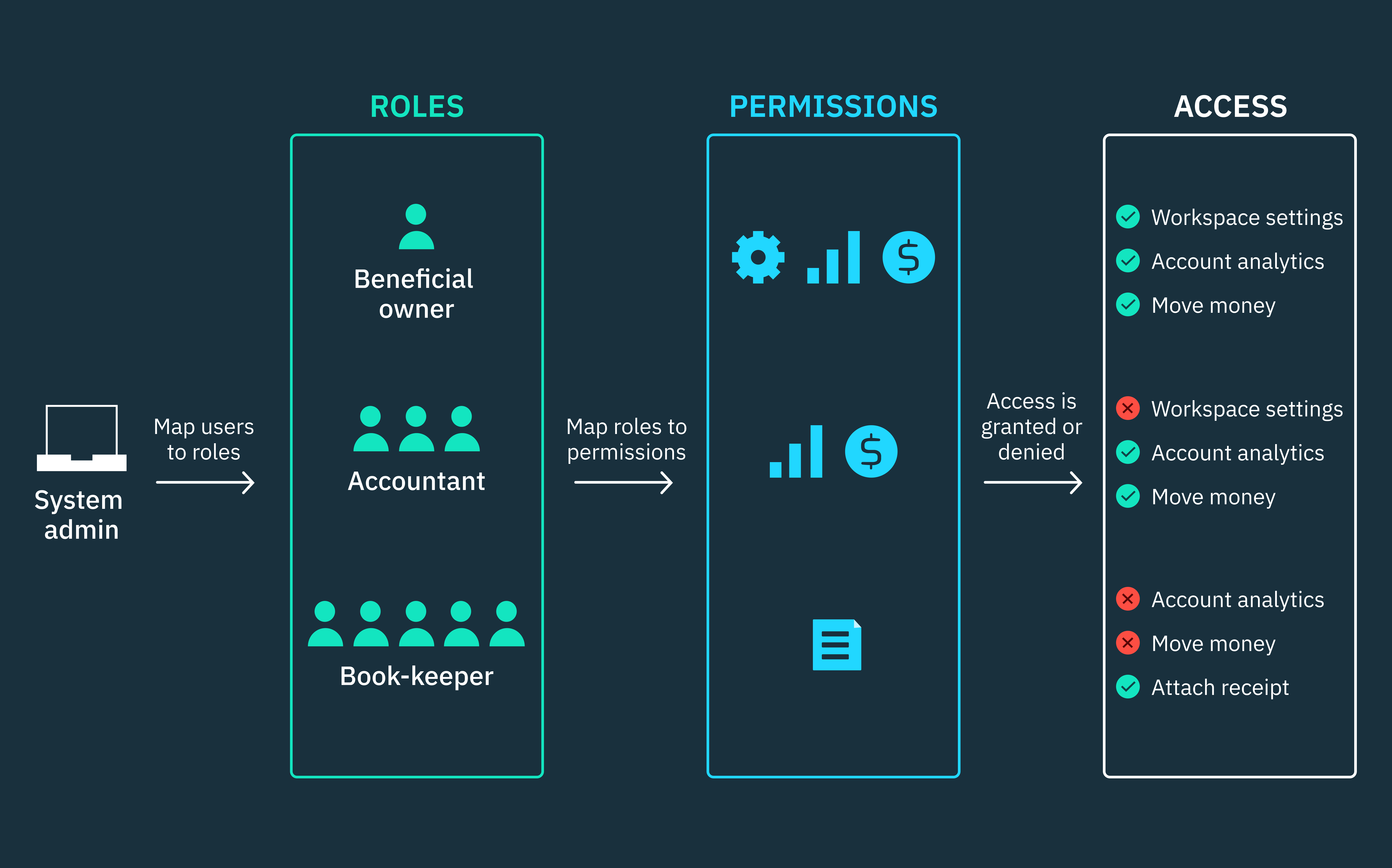
Role-Based Access Control (RBAC) has long been a cornerstone of Identity and Access Management, providing a structured and efficient way to manage user permissions. Its predefined roles make access management straightforward, especially for organizations with well-defined job functions.
However, as business environments become more dynamic, traditional RBAC models may face challenges in adapting to evolving access needs. Some common concerns include:
- Role Proliferation: Organizations often create an increasing number of roles to accommodate diverse access requirements, which can lead to administrative overhead.
- Static Role Assignments: Since RBAC relies on predefined roles, users may retain access even when their responsibilities shift, increasing the risk of excessive permissions.
- Limited Flexibility for Temporary Access: RBAC can struggle with short-term access scenarios, such as project-based contractors, third-party vendors, or remote employees needing temporary permissions.
To enhance RBAC, organizations can incorporate dynamic access mechanisms like Attribute-Based Access Control (ABAC). ABAC enables real-time access decisions based on user attributes, location, risk factors, and device health, ensuring access policies remain adaptive and aligned with security best practices.
A. How CloudEagle.ai Bridges the Gap
CloudEagle.ai enhances traditional RBAC by integrating context-aware access controls that help organizations strike the right balance between security and flexibility. With CloudEagle.ai, businesses can:
- Simplify Role Management by identifying and consolidating redundant roles, reducing administrative burden.
- Implement Just-in-Time (JIT) Access to grant temporary permissions for contractors, vendors, and employees, minimizing privilege creep.
- Leverage Risk-Based Access Controls to dynamically adjust permissions based on real-time security signals like user behavior and device health.
By combining RBAC’s structured approach with ABAC’s adaptability, CloudEagle.ai helps businesses create a scalable, secure, and efficient access management strategy that evolves with their needs.
a. Lack of Continuous Access Monitoring & Risk-Based Controls
Traditional Identity and Access Management solutions authenticate users at login but do not continuously monitor access behavior. As a result:
- Users maintain access longer than necessary, even after their roles change or they leave the company.
- Risky access behaviors go undetected.
- Compromised credentials can be used to escalate privileges without detection.
Modern security frameworks require adaptive risk-based access controls that can assess user behavior, device health, and location context in real-time to prevent unauthorized access attempts.
Furthermore, the increasing adoption of remote work and Bring Your Own Device (BYOD) policies introduces additional challenges. Employees often log in from personal devices, public Wi-Fi networks, or unmanaged endpoints, making it easier for attackers to exploit weak security measures.
Without continuous access monitoring, session analytics, and behavioral anomaly detection, traditional Identity Access Management systems fail to recognize and mitigate security threats proactively.
Organizations must adopt Identity Threat Detection and Response (ITDR) solutions that leverage AI-driven analytics to monitor real-time user behavior and detect suspicious activity before it leads to a breach.
b. Manual & Complex Access Reviews
Traditional IAM relies on periodic, manual access reviews, which are:
- Time-consuming: IT teams struggle to validate thousands of access requests manually.
- Error-prone: Reviewing access manually increases the likelihood of overlooking security gaps and unnecessary privileges.
- Compliance-intensive: Regulatory audits (e.g., SOX, GDPR, HIPAA) demand real-time access validation, which traditional IAM fails to provide, leading to compliance violations and penalties.
Manual access reviews typically occur quarterly or annually, which means security teams are often working with outdated access records. This lag creates a window of opportunity for attackers to exploit over-provisioned accounts, orphaned identities, and unauthorized access.
Additionally, lack of automation in access certification workflows forces IT and compliance teams to rely on spreadsheets and emails to track access approvals, making the process inefficient and vulnerable to human errors. Organizations need automated access reviews with AI-driven risk scoring to streamline audits, enforce compliance in real-time, and reduce administrative overhead.
4. The Rise of Modern Access Governance & Its Importance for CIOs
Today’s, Access Governance goes beyond traditional IAM by providing visibility, risk-based controls, and automation to ensure users have the right level of access at the right time.
A. Key Differentiators of Modern Access Governance
- Continuous compliance enforcement rather than periodic access reviews, ensuring organizations remain audit-ready at all times.
- Dynamic and context-aware access controls that adapt based on real-time risk assessments instead of relying on static role assignments.
- AI-driven access intelligence to detect and remediate risky permissions proactively, reducing the chances of security breaches.
- Comprehensive identity lifecycle management to ensure that users’ access rights change dynamically as their roles evolve.
- Access Governance enables security teams to establish granular policies and apply governance frameworks that reduce excessive access privileges, eliminate orphaned accounts, and enforce real-time access validation.
B. Why Access Governance Matters for CIOs?
With increasing regulatory scrutiny and sophisticated cyberattacks, CIOs must prioritize Access Governance as a core component of their security strategy. Traditional IAM solutions are no longer sufficient to meet modern compliance and security requirements.
C. Key Reasons Why CIOs Should Prioritize Access Governance
a. Prevent Identity-Based Attacks
- 80% of breaches involve compromised credentials.
- Detect & stop privilege escalation, insider threats, and unauthorized access.
b. Ensure Compliance & Audit Readiness
- Stay compliant with SOX, GDPR, HIPAA, ISO 27001.
- Automate access reviews & risk assessments to simplify audits.
c. Enable Zero Trust Security
- Enforce least privilege access, adaptive authentication, and JIT provisioning.
- Minimize attack surfaces & prevent lateral movement.
d. Reduce IT & Security Overhead
- Automate access reviews, certifications, and policy enforcement.
- Free IT teams to focus on high-priority security tasks.
e. Enhance Multi-Cloud & SaaS Security
- Secure AWS, Azure, Google Cloud, Salesforce, Workday, ServiceNow.
- Maintain consistent security policies across hybrid environments.
By investing in Access Governance, CIOs can enhance operational efficiency, reduce security risks, and improve compliance posture, ensuring a future-ready security strategy for their organizations.
5. Core Pillars of a Future-Ready Access Governance Strategy
A. Identity Lifecycle Automation
- Automate user onboarding, offboarding, and role transitions with workflow-based approvals to ensure secure and timely access.
- Use AI-driven role recommendations and Attribute-Based Access Control (ABAC) to dynamically adjust permissions based on behavior and context.
- Integrate HR and IT systems to automatically update access rights as employee roles change, preventing privilege creep.
B. Just-in-Time (JIT) & Adaptive Access Management
- Grant temporary access only when needed to minimize excessive privilege risks.
- Use contextual attributes (e.g., location, device trust, time of access, and risk score) to enable dynamic, policy-driven access decisions.
- Implement session-based access controls that automatically revoke permissions once tasks are completed.
- Deploy privileged access management (PAM) solutions to grant secure, time-restricted access for admin roles and critical systems.
C. Continuous Access Reviews & Policy Enforcement
- Implement real-time access certification rather than relying on periodic, manual reviews.
- Use automated access revocation to eliminate stale and excessive privileges before they become security liabilities.
- Enforce policy-driven least privilege access that dynamically adjusts user permissions based on behavioral analytics.
- Leverage AI-driven risk scoring to assess whether users should retain or revoke specific access rights.
- Automate audit trails and compliance reporting to ensure regulatory requirements are met without IT teams manually tracking access changes.
D. Multi-Cloud & SaaS Integration
- Unify access policies across on-premises, hybrid, and cloud environments to maintain consistency and security.
- Seamlessly integrate with SaaS applications like Salesforce, AWS, Google Workspace, and ServiceNow to streamline access management.
- Implement cloud-native identity governance solutions to avoid reliance on legacy on-prem IAM infrastructures.
- Ensure cross-cloud access federation to reduce the complexity of managing identities across multiple cloud providers.
E. AI & ML-Driven Access Intelligence
- Identify anomalous access behaviors using machine learning to detect potential insider threats and compromised credentials.
- Leverage user and entity behavior analytics (UEBA) to detect deviations from normal access patterns and trigger security alerts.
- Predict and prevent toxic access combinations (e.g., excessive admin privileges and finance system access) to mitigate segregation of duties (SoD) violations.
- Enhance real-time risk-based authentication by adjusting security measures based on ongoing user activity and behavioral insights.
- Automate remediation workflows to immediately revoke or modify risky permissions without requiring manual intervention.
6. How CIOs Can Implement an Access Governance Framework
To successfully implement an Access Governance framework, CIOs must first assess the current gaps and risks within their IAM infrastructure by,
A. Assess IAM Gaps & Risks
- Conduct an enterprise-wide access audit to detect orphaned accounts, excessive privileges, and role creep.
- Identify IAM inefficiencies in managing cross-functional access requests.
- Map identity governance gaps in compliance, enforcement, and security monitoring.
B. Adopt a Hybrid RBAC-ABAC Model
- Move beyond static RBAC to context-aware ABAC for fine-grained access control.
- Use attributes like job function, department, location, and risk score for dynamic access decisions.
- Implement policy-based provisioning to enforce least privilege access.
C. Leverage AI & Automation
- Automate access provisioning, revocation, and certification with AI-driven entitlement management.
- Detect anomalous access behaviors (e.g., unauthorized privilege escalation, inactive accounts).
- Enable risk-based authentication (e.g., step-up authentication for high-risk actions).
- Optimize workflow automation to reduce manual errors and improve efficiency. –v
- Maintain real-time access logs & audit trails for security visibility.
- Align policies with SOX, GDPR, HIPAA, ISO 27001, and NIST 800-53.
- Automate periodic access reviews to reduce compliance burden.
- Implement continuous compliance monitoring to prevent regulatory violations.
7. Future Trends in Access Governance
a. Trend 1
One of the key trends shaping the future of access governance is Identity Threat Detection & Response (ITDR). Integrating access governance with Security Operations Centers (SOC) enables real-time identity threat monitoring, allowing organizations to detect and respond to threats more proactively.
AI-driven threat modeling helps identify and mitigate insider threats, compromised accounts, and privilege misuse before they result in security breaches.
In addition, behavioral biometrics can be employed to enhance authentication security and prevent identity-based fraud, further strengthening access governance frameworks.
b. Trend 2
Another important development is the rise of the Unified Identity Fabric for Multi-Cloud & Hybrid Environments. As organizations increasingly operate across multi-cloud, on-prem, and hybrid environments, managing identities seamlessly across these platforms has become essential.
c. Trend 3
Federated identity management also plays a crucial role in reducing authentication silos and enabling seamless Single Sign-On (SSO) across enterprise applications.
d. Trend 4
Policy-Based Access Control (PBAC) is emerging and enhances as the next evolution beyond ABAC, allowing for business-driven, rule-based access provision tailored to organizational policies.
e. Trend 5
Enhancing Zero Trust Architecture (ZTA) with continuous authentication, micro-segmentation, and just-in-time access provisioning ensures that organizations remain resilient against cyber threats.
Implementing risk-adaptive access policies allows enterprises to dynamically adjust security controls based on evolving threats and user behaviors, strengthening their overall security posture.
8. Enhancing Role-Based Access Control (RBAC) with CloudEagle.ai
Role-Based Access Control (RBAC) has been the standard for managing user permissions, offering a structured approach to enforcing access policies. However, traditional RBAC models can struggle with role sprawl, static assignments, and limited flexibility for dynamic access needs.
A. Why CloudEagle.ai?
CloudEagle.ai transforms RBAC by integrating AI-driven automation, real-time monitoring, and adaptive security controls, ensuring organizations maintain a secure, scalable, and efficient access governance framework.
With CloudEagle.ai, businesses can:
- Automate Role Management – Reduce administrative overhead by identifying redundant roles and optimizing access policies.
- Enforce Just-in-Time (JIT) & Risk-Based Access – Grant temporary permissions for contractors, vendors, and employees while dynamically adjusting access based on security signals.
- AI-Powered Access Reviews & Compliance – Detect risky access behaviors, streamline access certifications, and ensure continuous compliance with security frameworks.
- Deep SaaS & Cloud Integrations – Seamlessly manage access across multi-cloud and hybrid infrastructures with pre-built integrations.
- Self-Service Access & Automated Approvals – Empower employees with AI-driven workflows that automate access requests and approvals, reducing IT bottlenecks.
By leveraging CloudEagle.ai, CIOs can modernize their identity security strategy, minimize compliance risks, and strengthen their Zero Trust approach to Access Governance, all while ensuring RBAC remains adaptive and effective in a dynamic enterprise environment.
9. Conclusion
Traditional IAM solutions are no longer sufficient to protect modern enterprises from evolving identity threats. Access Governance provides the missing layer of visibility, automation, and risk-based control needed to secure digital identities effectively.
By implementing a robust Access Governance strategy, CIOs can:
- Prevent security breaches by enforcing least privilege access and real-time risk assessments.
- Ensure continuous compliance with automated policy enforcement and audit readiness.
- Strengthen Zero Trust security frameworks by leveraging AI, automation, and adaptive access models.
- Enhance operational efficiency by eliminating manual access reviews and automating identity lifecycle management.
With CloudEagle.ai’s Access Governance capabilities, businesses can confidently navigate the complexities of identity security while ensuring efficiency, compliance, and resilience in an ever-evolving threat landscape.
10. FAQs
- Why is traditional IAM failing in modern enterprises?
Traditional IAM lacks scalability, automation, and dynamic security controls, making it ineffective in managing cloud and hybrid IT environments. - How does Access Governance differ from IAM?
Access Governance focuses on real-time monitoring, risk-based access control, and automation, whereas IAM primarily manages authentication and authorization. - What are the key benefits of Access Governance for CIOs?
CIOs can enhance security, streamline compliance, automate access management, and reduce insider threats with Access Governance. - How does CloudEagle improve Access Governance?
CloudEagle leverages AI-driven analytics, automated access reviews, and real-time risk assessments to enforce least privilege and improve security. - What role does AI play in modern Access Governance?
AI helps detect anomalies, automate access provisioning, and enforce policy-based access controls, reducing manual intervention and security risks.

%201.svg)





.avif)




.png)
.avif)






